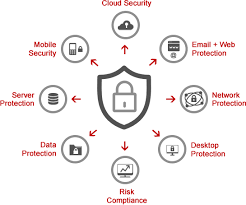
The protection of the technological infrastructure in organizations has become a priority, especially an endpoint security, as the weakest vector of the company.
And with a projected 175% increase in cybercrime by 2023, companies must learn the proper network security measures.
This prediction estimates that more than 33 billion records would be at risk of being stolen or breached in 2023 alone.
A figure is much higher than the 12 billion records that were stolen in 2018 by cybercriminals.
These figures are supported by the dedication to protecting servers and networks but leaving weak vectors in connections with other end devices because they are considered irrelevant.
It implies securing protection from the initial point of connection to the endpoint and associating services such as EDR Cloud to shield your company.
What is an endpoint?
For Kaspersky, endpoints (endpoint devices) represent any computer connected to the company’s network via the Internet.
This connection can be via wired, wireless, or fibre optic, regardless of whether the equipment is operated by a user or has an autonomy of operation in the company.
Currently, multiple endpoints can be achieved with the application of IoT and IIoT, both in homes, businesses, and industries.
Among the specific characteristics of these endpoints are that they have small computers with operating systems and software with different applications.
Also, many endpoints have certain specialized services such as:
- Webserver
- SSH
- FTP
- Wifi
- Bluetooth, among others.
These specifications are, practically, the mainstay of the vulnerability of the devices since they are susceptible to security issues through the “endpoint” attack vector.
Therefore, it attracts the attention of cybercriminals who may try to take control of them.
It is considered a weak vector of the organization since its importance is invisible to some users.
Endpoint Types
Without realizing it, our entire environment is connected in one way or another through various endpoints connected to a network.
Desktops, laptops, smartphones, POS systems, printers, scanners, and tablets are the most famous.
But many other devices are used to communicate with each other and share data in a connected environment.
Incibe-cert’s digital portal indicates that these devices are increasingly present in various environments, whether in vehicles, industrial equipment, health technologies, robotics, etc.
The Industrial Internet of Things (IIoT) in these devices allows them to expand their service and keep them communicating and exchanging information.
It is why, in ensuring endpoint security, the Security by Design (SbD) approach is beginning to be applied as an organizational standard.
This approach to endpoint management ensures that all endpoints on the network maintain certain levels of security.
Types of businesses with the most vulnerable endpoints
At this level, it can be deduced that any organization can be susceptible to a cybercriminal or malware attack in its endpoint security.
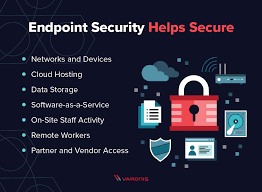
The leading companies that were affected by ransomware attacks on their endpoint devices are in the categories of:
In many cases, ransomware attacks require specialized endpoint security since most episodes are focused on these devices. There are various software development teams in Europe and the USA that can help with this.
But determining the most vulnerable business depends on how many endpoints the company has and whether these devices have a security system in place.
In some cases, even retail Point of Sale (POS) devices can be considered a highly vulnerable endpoint.
Although these POS can operate without an internet connection, the vast majority are online with the company’s servers and services so that prices, inventories, and sales can be updated immediately.
But more than the business, it is necessary to determine the type of endpoint and its characteristics that would imply the degree of vulnerability.
In this aspect, Incibe-cert raises the evaluation of the security measures of some components of the endpoints such as:
- Protocols. Having installed the appropriate configuration of the secure version of the protocol, for example, Secure DNP3 instead of DNP3, to improve authentication and encryption. Using techniques such as fuzzing, protocols can be tested to try to discover specific vulnerabilities.
- Ports and interfaces. The physical availability of interfaces (RJ45, WIFI, Zigbee, CAN, USB, etc.) can access the endpoint firmware. This input must be controlled physically (anti-tampering protection) and logically (disabling those not required or restricting access to identified users).
- Hardware access. Although somewhat related to the previous point, this one focuses more specifically on the operation of the internal parts and pieces of the endpoint. The security of these end devices in the physical access will prevent access to the inner features through anti-tampering protection that physically and logically blocks the device’s opening. In this aspect, some types of attacks can be mentioned as sophisticated or lateral, where attempts are made to modify values of the endpoint through alterations in the system clock signal or memory positions that are close to some circuits.
- Firmware. If a hacker gains access to the endpoint’s firmware, he can reverse engineer to find passwords stored in the code, weak or poorly implemented encryption algorithms. Today, this component can be updated from the web directly to the device.
- Software: Some industrial endpoints have sufficient computational capacity to compare them with the existing applications on a conventional server. For this reason, these devices must be evaluated to prevent them from having unnecessary or vulnerable programs installed.
Benefits of EDR Cloud for the endpoint
One of the ideal solutions for endpoint security is using an EDR Cloud service in the company.
It would centralize the security approach to a ubiquitous infrastructure, allowing connection and integration under pre-established protocols.
The implementation of the EDR Cloud service brings with it certain security features such as:
- Accurate detection of threats or false positives through the use of Artificial Intelligence (AI).
- Threat containment in a physical and virtual space, such as sandboxing, through the combined use of AI and Machine Learning (ML) to isolate in a safe risk environment and mitigate damage.
- Problem elimination and remediation through immediate incident response. This enables a rapid return to work activities after an attack.
- The investigation carried out by the IA and the ML allows the generation of records of the origin of the incidents, reducing attacks, and developing new protection strategies.
Conclusion
Endpoint security through the EDR Cloud is provided in a centralized manner since it distributes firmware and software updates and patches to all devices registered on the network.
If, for example, a device is not standardized to the policy guidelines, protocols can be established to limit access to essential data.
In this case, the EDR Cloud provider can monitor security systems remotely, automating them to simplify control processes.
Contracting the EDR Cloud service with a guaranteed provider will allow you to have more peace of mind in the business, knowing that your endpoints will be protected from potential threats. Below, you can learn more about the security of this vector with our product manager:
Another important aspect is that your endpoints will no longer be the weakest vector in the company, as they will be integrated under an extended protection scheme.
You will also incorporate new equipment into the network without requiring complicated updates or certifications since the control and monitoring will be centred in the Cloud.