As more businesses understood the inefficiency and inadequacy of traditional perimeter-based security approaches, they shifted data storage to cloud-native or hybrid infrastructures. When COVID-19 struck in 2020, it was clear that existing systems were inefficient for providing safe access to the remote workforce.
Many businesses had to speed up their digital transformation and find the right security solutions to provide safe access to the remote workforce. That’s when Secure Access Service Edge (SASE) was the best solution and still is. Let’s take a closer look at what is SASE and how it works.
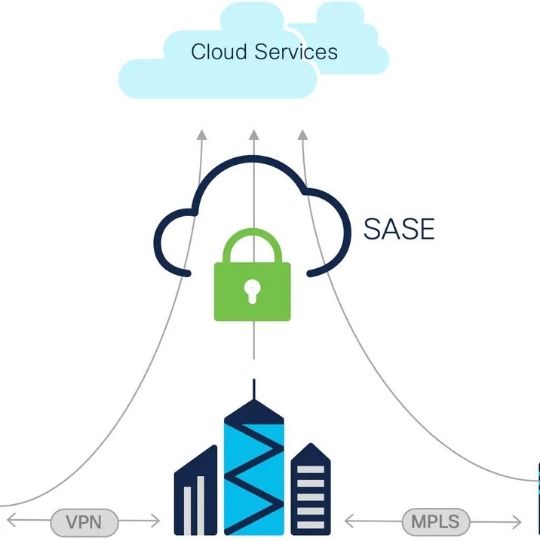
What Is SASE and How It Works?
Secure Access Service Edge (SASE) was introduced by Gartner in 2019. SASE is a cloud-native service that unifies the most enhanced security components and networking solution. It provides enhanced security and safe access to the corporate network regardless of location. With the SASE framework, all the end-points in your network are secure and always monitored. So, it enables greater visibility and control in your corporate network.
In SASE’s portfolio, there are five fundamental components, and these are SD-WAN as service, Secure Web Gateway (SGW), Firewall as Service (FWaaS), Cloud Access Security Broker (CASB), and Zero Trust Network Access (ZTNA). But, you can always add other security tools to the SASE portfolio. Let’s briefly explain fundamental components and their functionality in the SASE framework.
1- SD-WAN As Service
Software-defined Wide Area Network, is a virtual tunnel that directly connects end-points users to cloud applications and ensures safe access to the corporate network regardless of their locations. Additionally, it enables the best performance and improves network quality by distributing the network traffic across the WAN.
2- Secure Web Gateway (SGW)
Secure Web Gateway is responsible for distributing user-generated traffic across the cloud. Additionally, when there is heavy traffic in the cloud, it is harder to detect undesired malware. That’s why SGW always tries to maintain light traffic to detect malware and unwanted software. So, it always monitors and distributes traffic and searches for possible cyber threats.
3- Firewall as Service (FWaaS)
Firewall Service (FWaaS) is another layer of security on the cloud-native network perimeter. It is responsible for detecting unauthorized access and improving network security. Additionally, it protects all the end-points in the network perimeter and monitors all the traffic constantly.
4- Cloud Access Security Broker (CASB)
Cloud Access Security Broker (CASB) is responsible for monitoring the data flow between users and applications. Additionally, it enables all actions that are necessary for maintaining security policies.
5- Zero Trust Network Access (ZTNA)
Zero Trust Network Access is responsible for authenticating users and granting access to only authorized users. Additionally, it segments the network, gives limited access to users, and prohibits lateral movement. So, it reduces the surface areas of potential attacks and minimizes the impacts. In short, ZTNA provides enhanced network security.
Why You Should Care?
We live in a world where cyber threats increase every second, and malicious actors are around every corner, searching for vulnerable spots in your security. You should acknowledge that each successful attack can cost you millions of dollars and damage your reputation. That’s why you should consider implementing the SASE framework that provides enhanced security and enables secure access to end-point users. It is cost-effective, scalable, and easy to manage. If you want to learn more about this framework, you can check out, NordLayer guide to SASE.
Last Words
Secure Access Service Edge is the future of cloud-edge computing. It provides enhanced security and improved network performance. By adopting the SASE framework, you can save a lot of money and resources.