In recent months, Australia has been one of the worst sufferers due to ongoing cyber-attacks from remote places. Often, cyber frauds are difficult to apprehend because they indulge in these illegal activities from unknown places. They also constantly change their IP addresses and devices to confuse law enforcement agencies.
According to a report, cyber-attacks mostly take place in the form of software vulnerabilities. The software offers them backdoor entry through which they can easily invade the systems and servers of various people and organizations to demand ransom or money. There has been an over 25% increase in recent cases of software vulnerabilities across Australia. The only way to stay safe is to strengthen your system and software using the necessary antivirus tools and other safety solutions.
Before moving further, it’s important to understand what cybersecurity means and how you can enhance the safety of your online assets and data.
The Mystery of Dating in a Cyber-World
Cyber Security: Meaning And Perspective
Cybersecurity refers to the security mechanism to protect your hardware, networking devices, computer, and software from cyber-attacks. Data continues to be the most vulnerable part of cyber security systems. If your cyber security is compromised, there’ll be data breaches. Therefore, it’s essential that your cyber security system is up to date and you have taken the necessary precautions to keep your device and software safe.
As the culture of work-from-home and remote jobs is becoming popular, it has become everyone’s responsibility to ensure the 100% safety of their data, device, and credentials. Since most devices can be used for internet access, you must take maximum precautions to protect your device and data from cybercriminals.
Cyberattacks don’t have a definite pattern. Day by day, cybercriminals are getting smarter and more intelligent. You may never know when they will discover a new technique to deceive you. So, you should never share sensitive information online with anyone unless essential.
Here are some common types of CyberAttacks that can get you in trouble:
1. SQL Injection Attack

SQL stands for Structured Query Language. It is one of the commonest forms of cyber-attacks. Under this, the cybercriminal sitting from a remote location sends a malicious query to your device using your system’s IP number or other vulnerabilities, including data leakage. Then the device or server will reveal sensitive and confidential information through which cyber criminals can easily access your system using a remote hacking system.
Once they get access, cybercriminals can invade your system, steal sensitive information, and corrupt important files and folders using malicious codes.
2. Distributed Denial of Service (DDoS) Attack
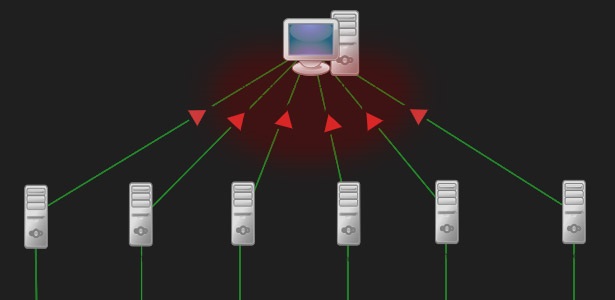
DDoS is another cyberattack that completely halts your work through unwanted traffic. It primarily affects the website, network system, and internet connection with unwanted traffic.
For example, if your business website receives 1000 views daily, and you find 50,000 new views one morning—it’s a clear case of a DDoS attack.
It will badly affect your website, and it may stop working until you secure your site. If you’re looking for 100% safety from cyber-attacks, installing Kaesim Cybersecurity solution is the need of the hour.
3. Phishing Cyber Attacks

Phishing attacks are rampant across the globe. There has been a considerable rise in the cases of phishing attacks after COVID-19. As the new norm of working from home and remote working gained momentum, cybercriminals secretly started using malicious tools and online codes to invade compromised systems and devices.
Outdated devices and systems with no antivirus tools installed are the most vulnerable ones. You should not conduct any banking-related transactions on these devices because remote hackers can easily track your activity, including stealing sensitive information like debit card numbers, online banking credentials, and your data.
Usually, all cases of phishing attacks are generated from online links. Therefore, if you find any suspicious email containing a link from an unknown email address, you shouldn’t click on it. Once you click a malicious link, your system will stop functioning, creating backdoors for the hackers to sneak in and get access to confidential information.
You shouldn’t click any suspicious links. Besides, you also need to ensure that your system is up-to-date and has an active antivirus tool installed.
In Conclusion
In the current scenario, you shouldn’t take any chance. You need to ensure that all your devices, especially those connected to the internet, are fully secure and safe. However, no user can confirm it. For this, you need to install a highly-effective cybersecurity solution on your devices for their full-proof security around the clock.




