Cyber Security

Cyber Security Informative Blog Technology
Checklist: Spring Cleaning Of Your Computer
The spring is the ideal season for an extensive interior and exterior cleaning of your house, with an emphasis on ...
Cyber Security Technology
The Ultimate Checklist For Ensuring Operational Technology Cybersecurity
When it comes to business processes and procedures, checklists are convenient. They help people stay disciplined and follow standard operating ...

Cyber Security
Backdoor Attack: Explaining Trojan, Ransomware & Malware
A backdoor attack is a vulnerability that facilitates cybercriminals to get unauthorized access to your system or network. Your sensitive ...
Cyber Security
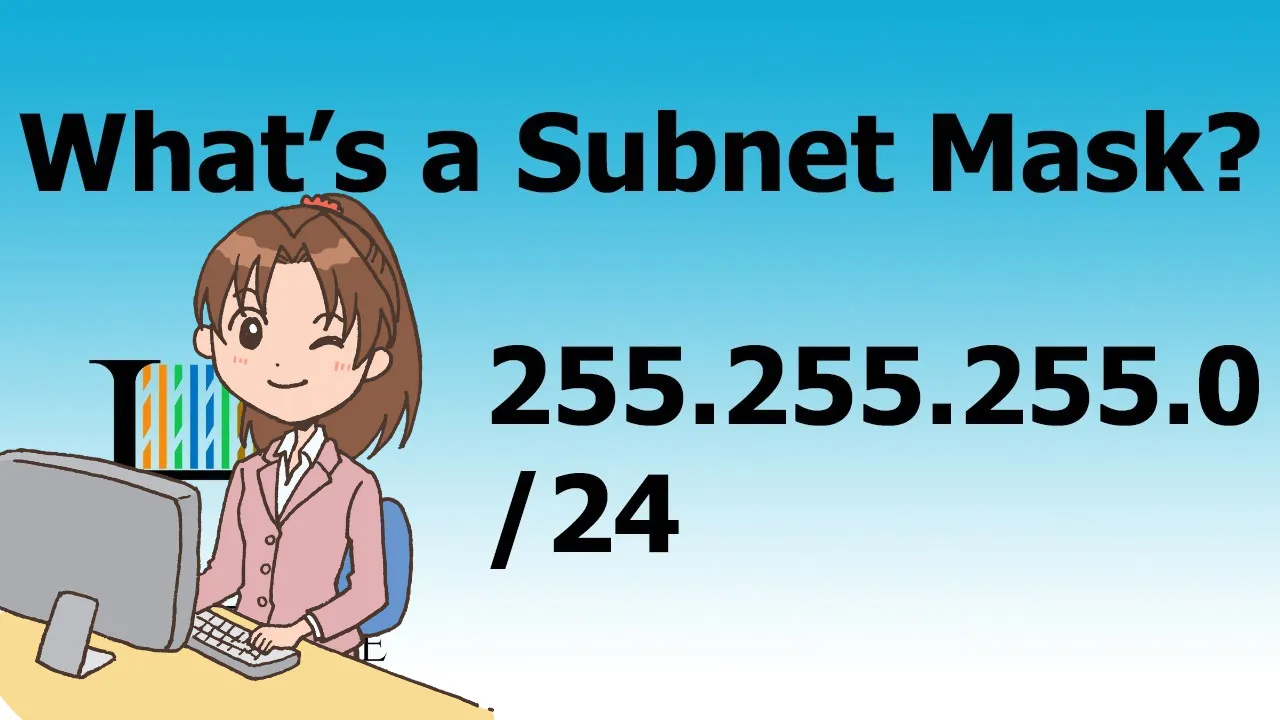
What Is My Subnet Mask & How Can I Find It Out?
A subnet mask is a numerical code dividing your internet communications into smaller subnetworks: the network and host. To answer ...

Cyber Security
How Should You Respond To The Theft Of Your Identity?
Is your identity used by another party because you upload your personal information and documents online? In this case, identity ...
Cyber Security
Network Security Key: How To Find It On 5 Different Devices?
Network security key is a password essential to connect to a wireless internet network. It serves as a secure link ...
Cyber Security
How To Turn Off SafeSearch On Different Devices: A Complete Guide
To turn off SafeSearch on your device, you disable the automated filter which blocks malicious content. There are several ways ...

Cyber Security
Norton LifeLock: Login. Subscription, And Pricing Plans
Norton LifeLock is a unique combination of identity protection with device protection, guaranteeing identity theft protection. Other services include Norton ...

Cyber Security Technology
How To Protect Your Social Media Accounts From Hackers
You’ve worked for years to make your online profile, share photos, and keep in touch with loved ones. But what ...

Cyber Security Technology
The Growing Importance Of Cyber Security In The Digital Age
Today we increasingly rely on digitization. Almost all aspects of our lives have been digitized, from shopping online to socializing ...

Cyber Security WhatsApp
WhatsApp Privacy: How To Enable And Disable End-To-End Encryption In WhatsApp
WhatsApp is now the preferred instant messaging service for smartphone users. Since Meta (Facebook) acquired WhatsApp a few years ago, ...
